

By Bill Hagerstrand, Director, Security Business, Marvell
Last year, Marvell announced that the Marvell LiquidSecurity family of cloud-based hardware security modules (HSMs) achieved FIPS 140-3, Level-3 certification from the National Institute of Standards and Technology. FIPS 140-3 certification is mandatory for many financial institutions and government agencies and, until then, had largely only been available with traditional self-managed, on-premises HSMs.
FIPS 140-3 certification also meant that cloud service providers could use LiquidSecurity HSMs to provide a wider range of security services to larger universe of customers.
Microsoft, which uses LiquidSecurity HSMs to power its Azure Key Vault and Azure Key Vault Managed HSM service, said it would begin to incorporate FIPS140-3 certified modules into its infrastructure.
This month, Microsoft began to offer single-tenant HSM services with FIPS 140-3 based services with LiquidSecurity in public preview.
“Every interaction in the digital world from processing financial transactions, securing applications like PKI, database encryption, document signing to securing cloud workloads and authenticating users relies on cryptographic keys. A poorly managed key is a security risk waiting to happen. Without a clear key management strategy, organizations face challenges such as data exposure, regulatory non-compliance and operational complexity,” Microsoft’s Sean Whalen wrote in the Azure Infrastructure blog. “An HSM is a cornerstone of a strong key management strategy, providing physical and logical security to safeguard cryptographic keys.
By Michael Kanellos, Head of Influencer Relations, Marvell
What happened in semis and accelerated infrastructure in 2024? Here is the recap:
1. Custom Controls the Future
Until relatively recently, computing performance was achieved by increasing transistor density à la Moore’s Law. In the future, it will be achieved through innovative design, and many of those innovative design ideas will come to market first—and mostly— through custom processors tailored to use cases, software environments and performance goals thanks to a convergence of unusual and unstoppable forces1 that quietly began years ago.
FB NIC on display at OFC
By Bill Hagerstrand, Director, Security Business, Marvell
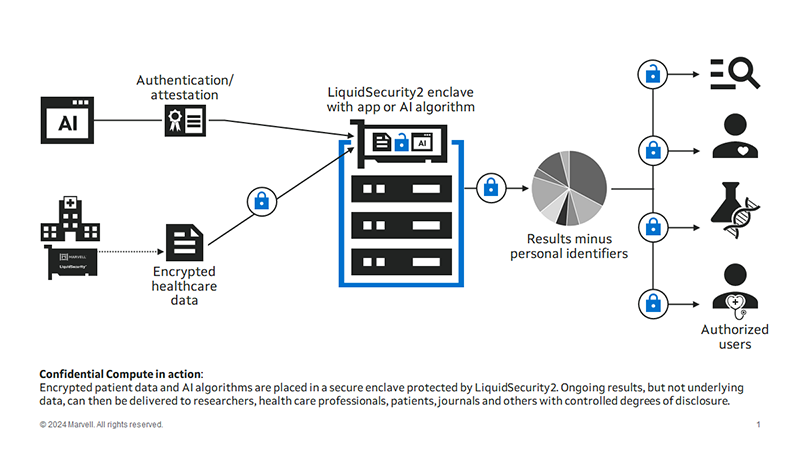
It’s time for more security coffee talk with Bill! I was first exposed to the term “Confidential Compute” back in 2016 when I started reading about this new radical technology from Intel. Intel first introduced us to this new idea back in 2015, with their 6th generation of CPUs called Skylake. The technology was named SGX (Software Guard Extensions), basically a set of instruction codes that allowed user-level or OS code to define a trusted execution environment (TEE) already built into Intel CPUs. The CPU would encrypt a portion of memory, called the enclave, and any data or code running in the enclave would be decrypted, in real-time or runtime, within the CPU. This provided added protections against any read access by other code running on the same system.
The idea was to protect data in the elusive “data in use” phase. There are three stages of data: at rest, in motion or in use. Data at-rest can be encrypted with self-encrypting hard drives—pretty much standard these days—and most databases already support encryption. Data in-motion is already encrypted by TLS/SSL/HTTPS/IPSec encryption and authentication protocols.
Data in use, however, is a fundamentally different challenge: for any application to make “use” of this data, it must be decrypted. Intel solved this by creating a TEE within the CPU that allows the application and unencrypted data to run securely and privately from any user or code running on the same computer. AMD provides a similar technology it calls AMD SEV (Secure Encrypted Virtualization). ARM, meanwhile, calls its solution Arm CCA (Confidential Compute Architecture). Metaphorically, a TEE is like the scene in courtroom dramas where the judge and the attorneys debate the admissibility of evidence in a private room. Decisions are made in private; the outside world gets to see the result, but not the reasoning, and if there’s a mistake, the underlying materials can still be examined later.
By Bill Hagerstrand, Director, Security Business, Marvell
Payment-specific Hardware Security Modules (HSMs)—dedicated server appliances for performing the security functions for credit card transactions and the like—have been around for decades and not much has changed with regards to form factor, custom APIs, “old-school” physical user interfaces via Key Loading Devices (KLDs) and smart cards. Payment-specific HSMs represent 40% of the overall HSM TAM (Total Available Market), according to ABI Research1.
The first HSM was built for the financial market back in the early 1970s. However, since then HSMs have become the de facto standard for more General-Purpose (GP) use cases like database encryption and PKI. This growth has made HSM usage for GP applications 60% of the overall HSM TAM. Unlike Payment HSMs, where most deployments are 1U server form factors, GP HSMs have migrated to 1U, PCIe card, USB, and now semiconductor chip form factors, to meet much broader use cases.
The typical HSM vendors that offer both Payment and GP HSMs have opted to split their fleet. They deploy Payment specific HSMs that are PCI PTS HSM certified for payments and GP HSMs that are NIST FIPS 140-2/3 certified. If you are a financial institution that’s government mandated to deploy a fleet of Payment HSMs for processing payment transactions, but also have a database with Personally Identifiable Information (PII) data that needs to be encrypted to meet General Data Protection Regulation (GDPR) or California Consumer Privacy Act (CCPA), you would also need to deploy a separate fleet of GP HSMs. This would include two separate HW, two separate SW, and two operational teams to manage each. Accordingly, the associated CapEx/OpEx spending is significant.
For Cloud Service Providers (CSPs), the hurdle was insurmountable and forced many to deploy dedicated bare metal 1U servers to offer payment services in the cloud. These same restrictions that were forced on financial institutions were now making their way to CSPs. Also, this deployment model is contrary to why CSPs have succeeded in the past, which was to offer when they offered competitively priced services as needed on shared resources.
By Bill Hagerstrand, Director of Security Solutions at Marvell
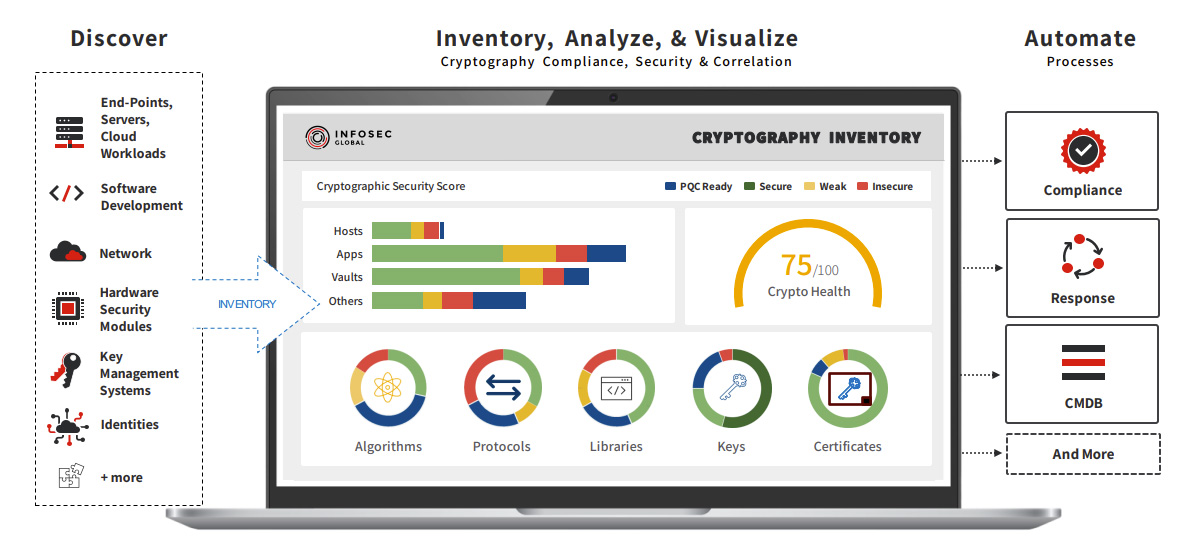
InfoSec Global, a leader in cryptographic agility management analytics software, and Marvell, a leader in Cloud based HSMs (Hardware Security Modules), have partnered to enable visibility and security in the cloud.
The Marvell® LiquidSecurity® family is a solution of hardware security modules (HSMs) based on a PCIe form factor instead of traditional 1U and 2U pizza boxes They are purposely designed to enable CSPs (Cloud Service Providers) to offer security services in a cloud environment. Not only does the smaller form factor and optimized processing of LiquidSecurity provide a path to reduce the cost, overhead, and rack space needed for performing encryption and key management, partitions and others performance features enable clouds to serve a large number of customers in a flexible manner.